The Hidden Matrix: Trust Infrastructure of an Empire
In my search for cohesive trust studies, I keep returning to an uncomfortable example: the Mongol Empire. Uncomfortable because while I acknowledge the immense suffering it caused, I cannot ignore what it teaches us about trust at scale.
Modern organizations struggle to maintain trust across time zones, even with advanced digital tools. The Mongols managed it across continents using human riders. Companies today grapple with digital authentication challenges. The Mongols solved similar challenges using physical tokens and human networks. We, as a civilization, have been designing distributed systems to handle modern trust challenges, but Genghis Khan did something unbelievable, taking many tribes and warlords and incentivizing them, maybe engineering them to a very robust trust community.
The Physical Foundation
The Shared danger experienced in fighting isn't just team building—it's more like proof of concept in system design. When two potential opponents have to trust each other with their lives, it creates a working prototype of trust that can then be scaled. If the trust works in life-or-death situations, it validates the potential for broader cooperation. The Mongols built their empire's trust infrastructure on this foundation of physical presence and shared vulnerability. The Mongols initiated their empire on a foundation of physical presence and shared vulnerability.
This isn’t accidental. Genghis Khan systematically created situations where traditional opponents had to trust each other with their lives. In my years in the dojo, I've seen how physical shared experience, an experience that is engineered correctly, creates trust bonds that words cannot. The Mongols scaled this principle to empire-building.
The Trust Protocol
What emerged was something remarkable: an operating system for maintaining trust of many “nodes” across vast distances. The Yassa code wasn't a moral law—it was a protocol for specific, highly advanced, human cooperation. Like modern distributed systems, it had to solve fundamental problems of authentication, validation, and consensus.
Consider the famous Mongol messenger system. On one level, it was just a sophisticated courier network. But look closer, and you see something that parallels our most advanced distributed systems: methods for validating messages, detecting fraudulent actors, and maintaining consensus across vast distances without instant communication. Just to pepper this with history, Ogodei Khan stopped a successful European campaign and returned to the Khanate because he got a message that Ghengis Khan died. He could have distrusted the messenger or trusted the messenger but used the power vacuum for personal ambition, but he didn’t. That’s a credit to him and to the protocol Ghengis Khan engineered. This example demonstrates for me how the Yassa protocol and messenger system created a framework where even personal ambition was tempered by trust in the system.
The Hidden Matrix
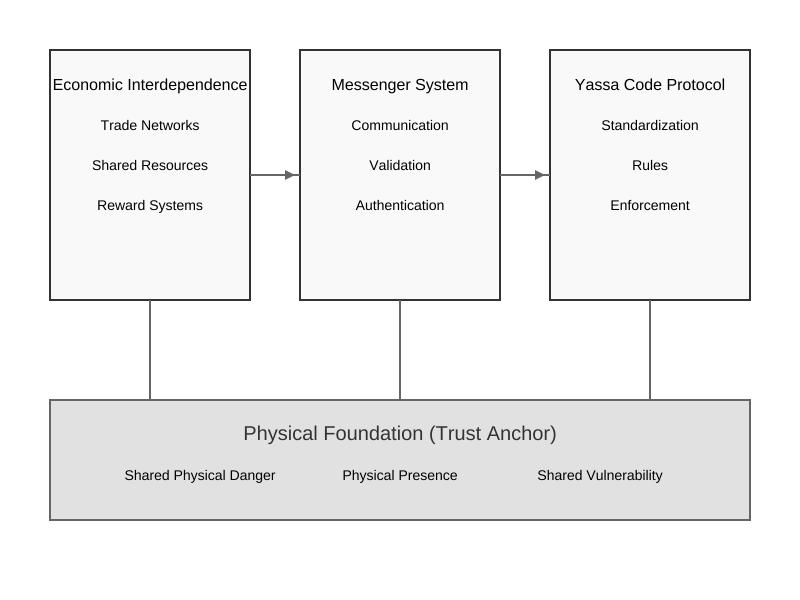
The true genius of the Mongol system wasn't in any single component. It was in how everything interlocked to build trust—a hidden matrix where physical, economic, and psychological elements reinforced each other. Like nodes in a neural network, each element strengthened the others:
- Physical presence established trust anchor—the foundation layer where human data processing is richest
- Economic interdependence incentivized trust cooperation—creating tangible long time rewards for maintaining the trust network
- The messenger system provided the most important trust ingredient - trustable communication across vast distances
- The Yassa code standardized it all into a protocol that could scale
In this matrix, physical danger validated trust, economic benefits sustained it, and the messenger system scaled it. Each element was both input and output in a complex system of human cooperation.
This wasn't just a warring exploitative empire. It was a trust protocol that operated successfully at a scale we still struggle to achieve today.
Modern parallels
When we design distributed systems today, we grapple with similar challenges:
- How do we maintain trust without central authority?
- How do we detect and handle bad actors?
- How do we ensure authentic communication across vast networks?
The solutions may look different—cryptography instead of courier tokens, digital signatures instead of physical seals—but the underlying problems remain remarkably similar.
Questions Worth Asking
As we build our modern trust systems, perhaps we should ask:
The Mongol Empire's trust infrastructure survived challenges that would cripple most modern systems. As we build systems for tomorrow, I want to remember the ancient lesson of trust at scale: communication, interdependence, and shared purpose can transform disparate factions into resilient networks.